Universal Cloud Service - Streamline Your Operations Globally
Take Advantage Of Cloud Solutions for Enhanced Information Security
Leveraging cloud services provides a compelling remedy for companies seeking to strengthen their data security steps. The question emerges: just how can the usage of cloud solutions reinvent data safety methods and give a robust shield versus prospective vulnerabilities?
Significance of Cloud Security
Making sure durable cloud safety steps is extremely important in securing delicate data in today's electronic landscape. As organizations progressively rely on cloud solutions to store and process their information, the requirement for solid security methods can not be overstated. A violation in cloud security can have serious consequences, ranging from economic losses to reputational damage.
One of the main reasons cloud security is critical is the shared responsibility design used by the majority of cloud solution providers. While the provider is in charge of securing the facilities, consumers are in charge of securing their data within the cloud. This department of duties highlights the significance of carrying out durable safety and security measures at the individual level.
Moreover, with the spreading of cyber risks targeting cloud atmospheres, such as ransomware and information violations, companies have to remain proactive and alert in mitigating risks. This involves on a regular basis upgrading safety methods, checking for dubious tasks, and informing workers on best practices for cloud safety and security. By prioritizing cloud protection, organizations can better safeguard their delicate information and maintain the trust of their stakeholders and consumers.
Information Security in the Cloud
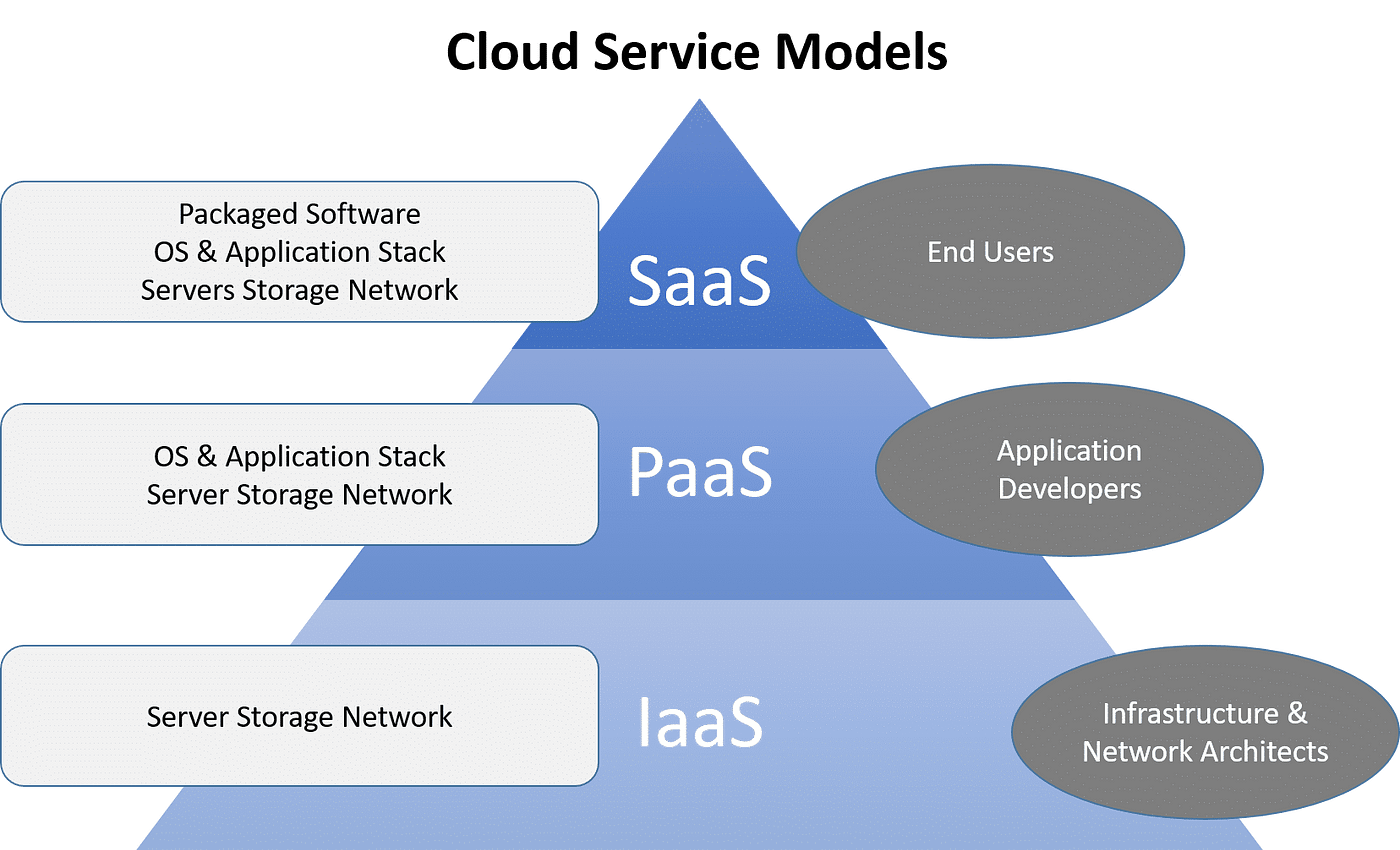
Security in the cloud normally entails the use of cryptographic formulas to rush information right into unreadable formats. Additionally, lots of cloud service providers offer encryption systems to secure data at rest and in transit, improving overall data defense.
Secure Information Backup Solutions
Data back-up solutions play an important function in ensuring the resilience and security of information in case of unforeseen events or data loss. Safe and secure information backup services are essential parts of a durable data protection method. By regularly supporting data to safeguard cloud web servers, organizations can mitigate the risks related to data loss as a result of cyber-attacks, hardware failures, or human mistake.
Executing safe data backup solutions includes picking reputable cloud service suppliers that supply file encryption, redundancy, and data honesty measures. In addition, information honesty checks ensure that the backed-up data remains tamper-proof and unchanged.
Organizations should establish computerized backup schedules to make sure that data is continually and successfully backed up without hands-on intervention. When required, routine screening of information repair procedures is likewise important to ensure the efficiency of the back-up remedies in recouping data. By purchasing secure information backup remedies, check these guys out companies can enhance their data safety position and decrease the effect of prospective data violations or disturbances.
Duty of Access Controls
Executing rigid gain access to controls is important for keeping the security and integrity of sensitive details within organizational systems. Gain access to controls function as an essential layer of protection versus unapproved gain access to, guaranteeing that only licensed individuals can check out or control sensitive information. By defining that can gain access to certain resources, companies can restrict the threat of data violations and unauthorized disclosures.
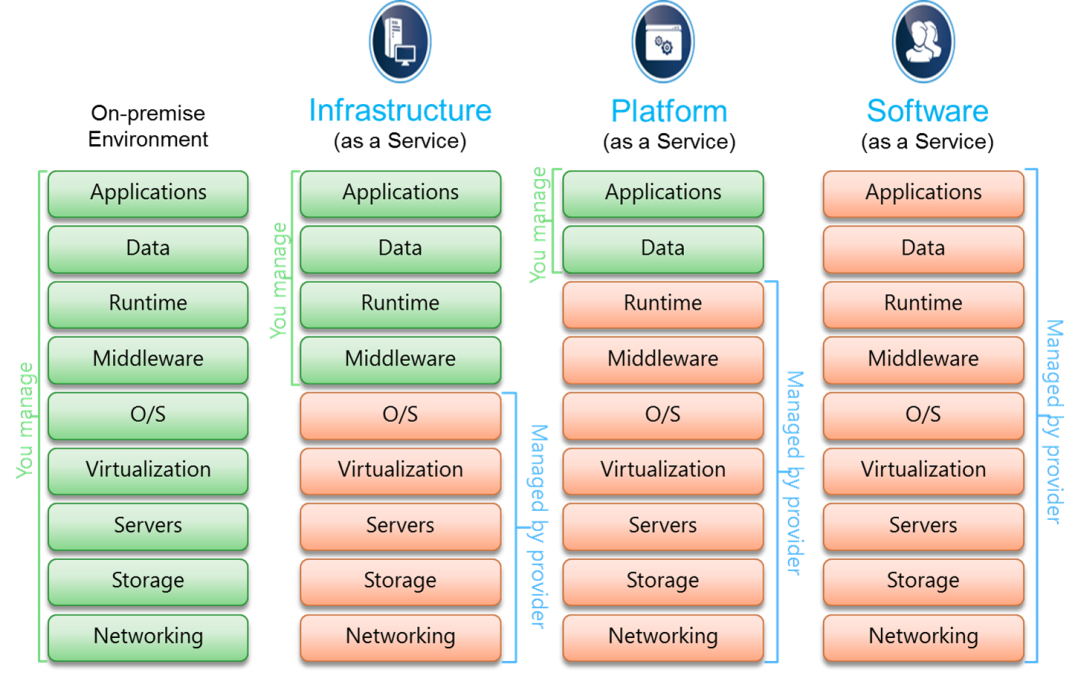
Consistently updating and assessing gain access to controls is vital to adapt to organizational changes and advancing safety risks. Constant monitoring and bookkeeping of gain access to logs can help spot any kind of dubious tasks and unapproved gain access to efforts immediately. In general, robust access controls are essential in protecting delicate information and mitigating protection risks within business systems.
Conformity and Regulations
Regularly making sure compliance with appropriate regulations and requirements is important for organizations to support information safety and security and personal privacy measures. In the realm of cloud services, where information is frequently kept and processed on the surface, adherence to industry-specific regulations such as GDPR, HIPAA, or PCI DSS is important. These policies mandate details data managing methods to secure delicate information and guarantee customer personal privacy. Failing to conform with these laws can lead to severe charges, consisting of fines and lawsuits, harming an organization's track record and trust.
Lots of companies use encryption capacities, gain access to controls, and audit routes to aid organizations fulfill data protection standards. By leveraging certified cloud services, companies can enhance their information safety posture while fulfilling regulatory commitments.
Verdict
To conclude, leveraging cloud solutions for improved information safety and security is crucial for organizations to shield sensitive info from unapproved gain access to and possible breaches. By carrying out durable cloud safety and security methods, including information encryption, protected back-up services, accessibility controls, and conformity with policies, organizations can take advantage of sophisticated protection steps and competence used by cloud provider. This assists mitigate dangers properly and ensures the discretion, stability, and accessibility of information.

Information backup solutions play a crucial role in making sure the strength and safety of data in the occasion great site of unforeseen occurrences or data loss. By regularly backing up information to secure cloud web servers, companies can reduce the threats connected visit here with information loss due to cyber-attacks, equipment failures, or human mistake.
Carrying out secure data backup services entails selecting dependable cloud solution providers that use encryption, redundancy, and information honesty actions. By investing in secure data backup options, companies can boost their data safety position and reduce the impact of prospective information breaches or disturbances.